
Check First analysts have reconstructed the structure and functions of the information operations troops (VIO) of the GRU.
The study combines OSINT analysis with phaleristics, i.e., the study of military awards, chevrons, pennants, and commemorative badges.
Analysts collected and analyzed 118 photographs of award symbols associated with Russian military intelligence units, enabling them to identify the units’ specializations, subordination, and geographic locations.
According to Check First’s findings, most of the key parts of the VIO date back to the Soviet period and have existed for decades as cryptographic, technical, or propaganda units.
As a result of the analysis, researchers identified at least 15 units within I&O and grouped them into three main areas: psychological operations, decryption and cryptanalysis, and computer network operations.
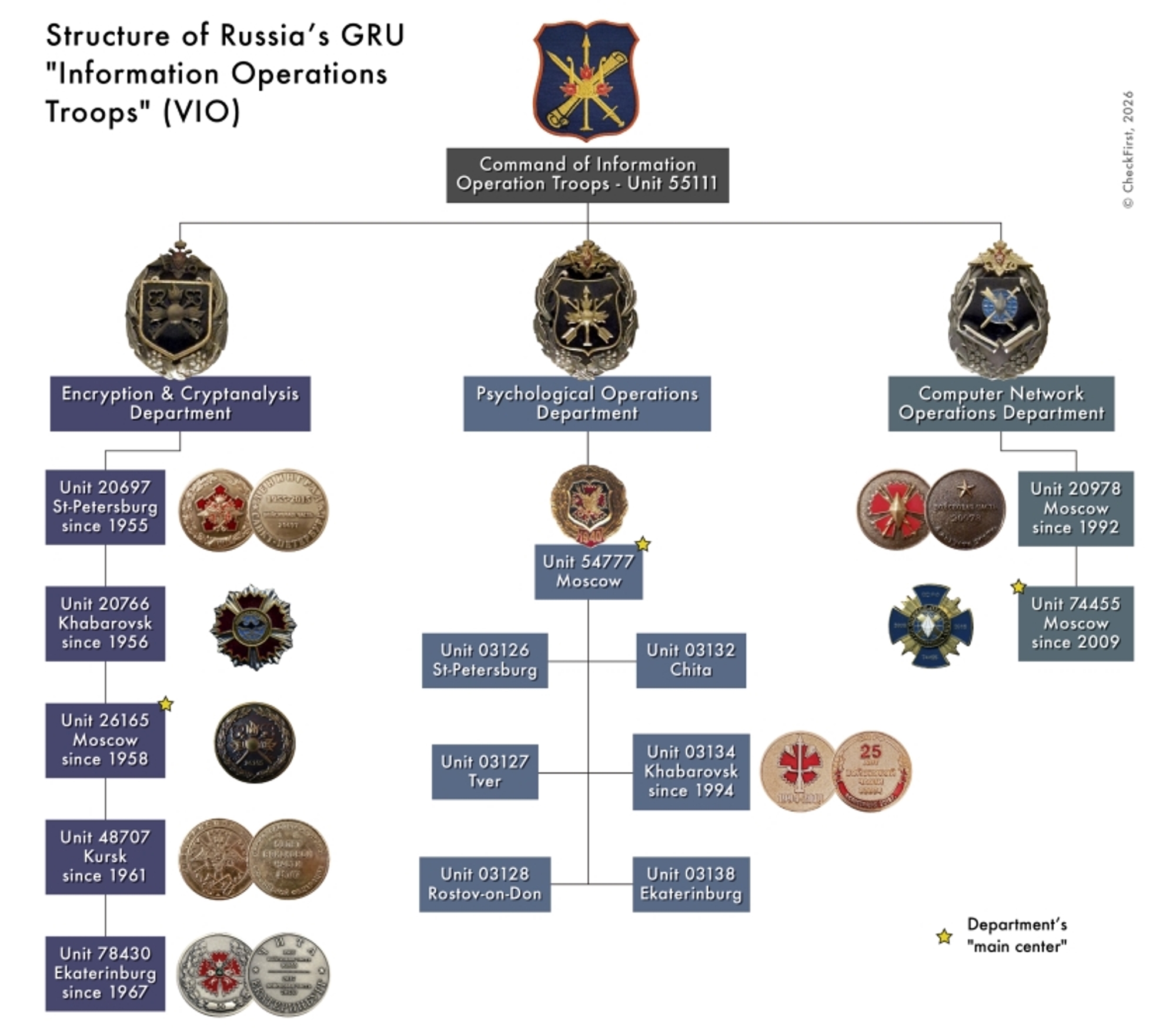
Analysts identify Military Unit 54777 as the central element of psychological operations, serving as the primary center of the Information Operations Directorate within the GRU.
Western intelligence services have previously linked military unit 54777 to information campaigns against Ukraine, the US, and NATO countries, and the Check First study confirms its systematic role within the Information Operations Directorate.
In addition to the central unit, the Information Operations Directorate comprises a network of regional psychological operations units, including military units 03126, 03127, 03128, 03132, 03134, and 03138.

An analysis of awards shows that these units share common symbols and organizational logic, but are focused on different geographical areas, including Ukraine, NATO countries, Asia, and domestic audiences in the Russian Federation.
The second key component of VIO is decryption and cryptanalysis units, which are formally responsible for communications security but have in fact become the basis for Russia’s offensive cyber operations. Decrypters decipher intercepted encrypted information.
Analysts attribute military unit 26165 to this area, known in Western investigations as the base of the APT28 (Fancy Bear) hacker group, which has been involved in numerous cyberattacks against foreign states.
In addition to 26165, the analysis of awards has confirmed, for the first time, the affiliation of several less-public units with the VIO, namely 20697, 20766, 48707, and 78430.
The report notes that these units provide the cryptographic, technical, and personnel basis for operations in cyberspace and work closely with psychological operations.

The third branch of the VIO — computer network operations — is responsible for direct hacking, sabotage, and technical preparation of attacks, which are subsequently reinforced by information campaigns. Military unit 74455 was identified within the structure.

The study emphasizes that Russian military doctrine does not distinguish between cyberattacks and propaganda, viewing them as a single space of “information warfare.”
That is why PSO operates as an integrated system, where technical incidents, data leaks, and infrastructure failures are used to achieve psychological and political effects.
Analysis of award symbols also enabled partial reconstruction of the chains of command and the probable locations of units in Moscow, St. Petersburg, Kursk, Yekaterinburg, Khabarovsk, and other cities in the Russian Federation.
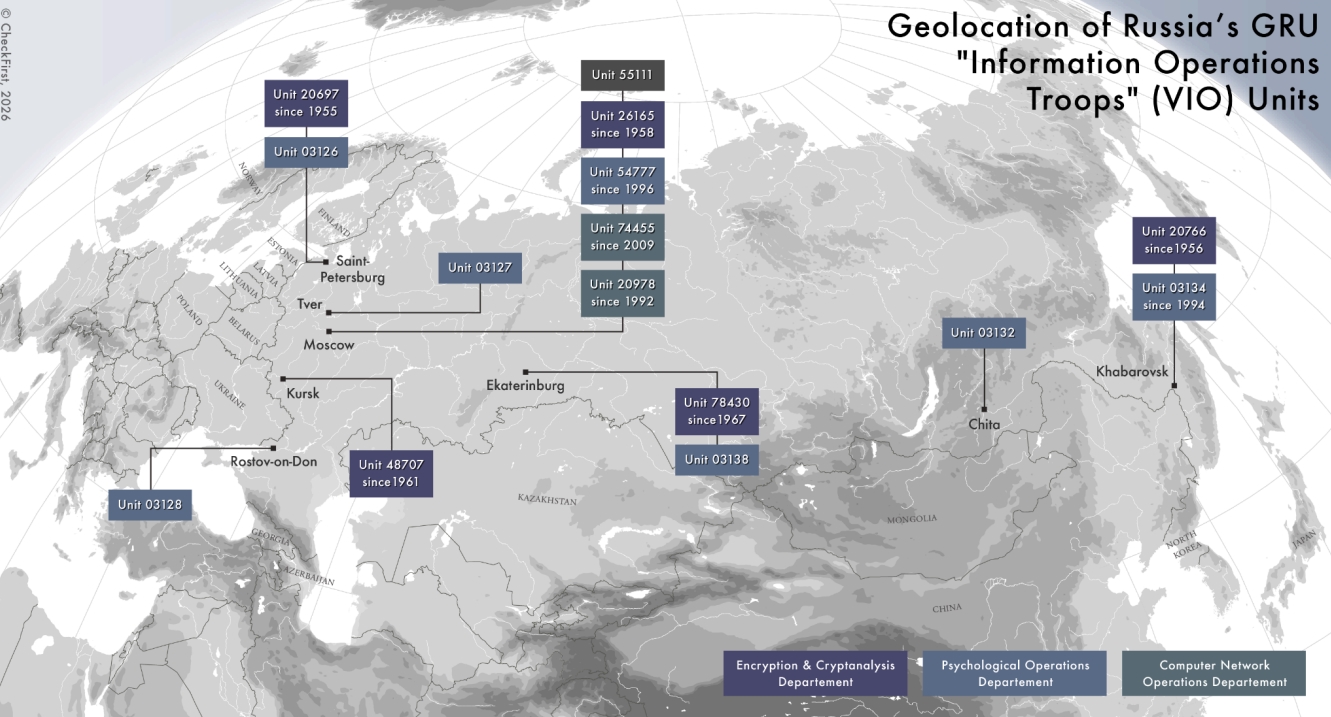
The researchers pay particular attention to the possible headquarters-level command of the Information Operations Directorate, which may be linked to military unit 55111, which does not have its own public award symbols.
The authors of the report emphasize that understanding the real forces of information operations is critical to countering Russian cyber and information operations.
Last year, Check First published a report analyzing the infrastructure of the 16th FSB Center, based on a year-long study.
Підтримати нас можна через:
Приват: 5169 3351 0164 7408 PayPal - [email protected] Стати нашим патроном за лінком ⬇
Subscribe to our newsletter
or on ours Telegram
Thank you!!
You are subscribed to our newsletter